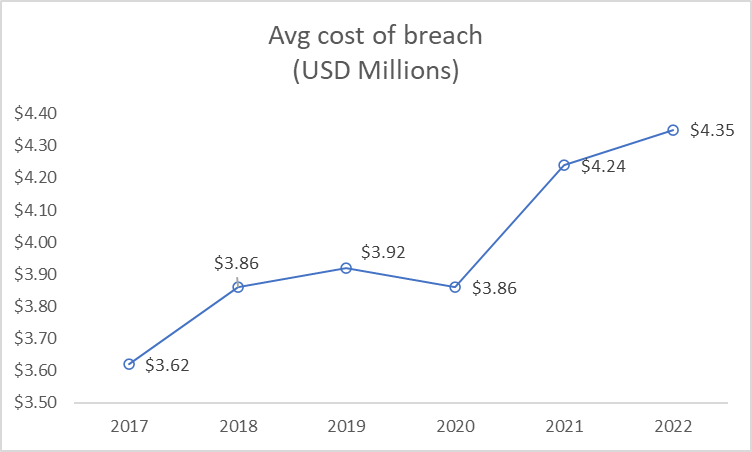
(Chart based on data from IBM Cost of data breach report)
According to IBM’s latest Cost of a data breach report, $4.35M is the the average cost of a data breach, with US costs exceeding $9M! If you want to avoid some hefty expenses, and a lot of headaches, this article will help educate you on ways to mitigate the risk of a data breach.
Introduction
I get it, as business owners, we have so much on our plate, security tends to be the last thing we think about. In this article I’m going to explain why it’s important for every business owner to learn about Cybersecurity. With the right practices, it doesn’t have to be expensive or complicated to significantly reduce the risk of a breach.
Many people believe that they are safe because hackers are only after “the big guys.” But as I wrote about in a previous article, hackers are mostly motivated by money. They don’t necessarily care where that money comes from.
Also, hackers are just as lazy as anyone else, so they are going to take targets of opportunity when presented. This means they are going to work the minimum amount required to perform a breach. If and when your business presents an easy way to be breached, that is exactly when you will be.
So let’s dig in a bit deeper into how security breaches happen. Then we’ll talk about what can be done about it, and how to protect your business.
How breaches happen
According to the Verizon Data Breach Investigations Report (DBIR) for 2022, credentials and phishing accounted for some 65% of breaches in 2021. See the screenshot below:
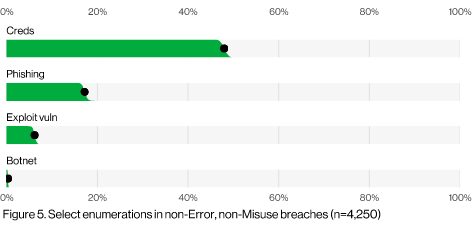
(From: Verizon DBIR 2022)
This means the majority of breaches occurred not because of sophisticated hacking techniques. Instead, hackers were able to get in either because someone used a weak password, or fell victim to phishing (also known as business email compromise).
These are targets of opportunity which do not require significant effort to perform. Because of the ease of execution, and these types of attacks continue to work well, we continue to see the same attacks in the wild.
As a business owner, and a Cybersecurity professional, these two vectors are simultaneously the hardest, and the easiest to prevent. How can that be true? Well it turns out that no amount of security tools can be thrown at the problem to solve it. These problems can only be solved by effective employee training and security awareness. So let’s dig into this a bit more.
What can be done
Implementation of a good security strategy for the organization is the best solution to preventing a security breach. I know what you’re thinking now, “here we go, this is the part where we are supposed to do all that boring security stuff that makes everything more difficult.”
First of all, security isn’t boring, at least I don’t think so; ok maybe I’m biased a little on this subject. But if your security program is boring and difficult, then chances are it’s not going to work well for your business. As I’ve discussed before, good security professionals know that people will find ways around difficult practices to avoid the extra work.
Here are a few basic steps you can take to build a good security foundation for your business:
- Find a good security training program.
- Limit use of passwords whenever possible.
- Add Multi-Factor Authentication (MFA) to your apps.
- Use a password management solution when required.
Let’s dive into each of these items in a bit more detail to see how each can help you build a solid security foundation.
Security Training Program
A security training program is one of the best ways to get started. Adding security awareness for your employees helps them understand why security is an important topic. As we saw earlier, 65% of attacks involved people in some way. If you can reduce the chance your employees will accidentally click on the wrong link, you might just save yourself a lot of time and money.
A good security program should have a few key elements:
First, it should be entertaining; if it’s too boring to watch/read/etc. then nobody will pay attention too it. I get it, security is a boring topic, but that doesn’t mean your training program needs to designed for robots. You’re not training employees to be security engineers; a 30-60 minute training should be more than sufficient for your needs.
Second, it should cover the typical cyber threats experienced. These include phishing, SMishing, business email compromise, and other similar threats. Also, some industries have more specific threats that should be covered as well. For example, the medical industry frequently deals with cryptolocker attacks. Find out what kinds of attacks occur in your industry, and be sure your awareness program covers those as well.
Finally, it should cover the details of your security program. If you have any security applications in place, let users know what those are. It should cover any security policies that you have in place and where users can find additional info. Last, if you have any mechanism for reporting suspicious activity, make sure your training program covers all of those as well.
Limit passwords
For those outside of the Cybersecurity community, this may come as a bit of a shock: Passwords are not a good security practice. That may be hard to understand since most likely every website you use requires you to enter a password. Let’s talk about why that is the case a little bit.
Nobody really likes using passwords. They are tedious, and it’s impossible to remember more then a few of them. So most people tend to have a few passwords they use. When it comes time to rotate passwords, they do something like add an exclamation point, or increment the number in their password. If this sounds familiar, don’t feel bad, I would be lying if I said I’ve never done this myself.
But here’s the problem: hackers know that people do these things. There is an entire sub-attack which focuses on taking known passwords and applying these types of practices to identify new passwords. This means if your old password has ever been leaked online, a hacker could take that and start incrementing that number or adding exclamation marks and identify your new password very easily. Let’s face it with all the security breaches, there is a good chance your password is already out there somewhere, waiting to be used by an attacker.
So what do you do about this? Use Facial recognition as a login mechanism instead. Most modern phones and computers allow some form of Face ID. It is not only more secure, it’s also more convenient. Learn how to use the solution that works for your computer, and implement it. Some business systems are starting to piggy back off of these built-in solutions as well, find out which ones you use today and make the switch. For those that don’t, make a feature request to your vendors for that functionality.
Multi-Factor Authentication (MFA)
MFA is a great way to add a layer of security when logging into your companies applications. If you combine Face ID and MFA the process for logging in can be quick and easy as well. Most of the modern implementations of MFA rely on an app installed on your phone which relies on Face ID as well.
Here’s why this is super helpful: if a hacker somehow manages to steal your password for a website, they can’t login until you approve it with your phone. This is where security training becomes critical for your employees as well. They need to be aware that if a popup for MFA occurs on their phone randomly, there’s a chance that is an attacker trying to login to something. But don’t freak out yet, often it’s just a background browser tab which needed to re-login.
There are many solutions for MFA on the market today, many of them are part of a Single-Sign-On (SSO) solution as well. SSO is a great way to let your users login with a single authentication mechanism and limit the use of bad password practices across all of your applications.
MFA and SSO can be difficult to implement, so it’s best to consult a technical professional to avoid complications. However, these solutions are getting easier and easier to implement. This means implementing a solution shouldn’t break your bank account. If you are interested in learning more, contact us for a consultation today!
Password Vaulting Solution
So as of the time this article was written, we are still a long way from leaving passwords behind entirely. There are still millions of websites that rely on passwords today, and even the ones which allow Face ID tend to use passwords as a backup. So what about all of those?
As we discussed above, passwords suck. But it doesn’t mean you can’t make password usage really secure, and easier at the same time. Enter a password vaulting solution.
Password vaulting tools allow you to create a unique randomly-generated and highly secure password for every website you use. The passwords are stored within a securely encrypted vault. Here’s the best part: the vaulting software makes the login process easier by auto-filling your username and password details each time you visit a website.
I’ve written about password vaulting tools previously, from the context of your personal computer. But there are also many solutions designed for businesses. Systems designed for businesses have features like team sharing, user management, and in some cases automated password rotation. They may even prevent your employees from seeing passwords, or be integrated with your SSO or MFA solutions.
I will write more extensively about vaulting solutions for businesses in a future article. Make sure you follow my articles to be notified when it comes out!
Conclusion
Ok I covered a lot in this article, if you stuck with me all the way through, that’s awesome! You now know way more than most business owners about how to keep your business secure!
Let’s quickly recap what we’ve learned:
- 65% of data breaches are directly linked to credentials and phishing
- These types of attacks typically occur because of bad password security or lack of security knowledge
- There are four basic steps any business owner can take to create a foundation of good security:
- Implement a good security training program
- Don’t rely on passwords – use Face ID
- Implement multi-factor authentication
- When passwords are required – use a password vault
But let’s be honest: this is not the end of the security journey. There are many more security topics to cover. I also would not recommend implementing an entire security program by yourself.
I will provide more security information for business owners on a regular basis. If you are a business owner who wants to stay updated on Cybersecurity topics, follow me on social media, or sign up for my newsletter.
References
https://www.ibm.com/reports/data-breach
https://www.verizon.com/business/resources/reports/dbir/