Most people think hackers are only targeting big banks or other larger financial institutions. While it is true in some cases, they are premium targets, this is not always the case. The motivations behind hackers has largely boiled down to a handful of reasons.
Let’s take a quick look at the top reasons for why attacks take place and why security is important for everybody.
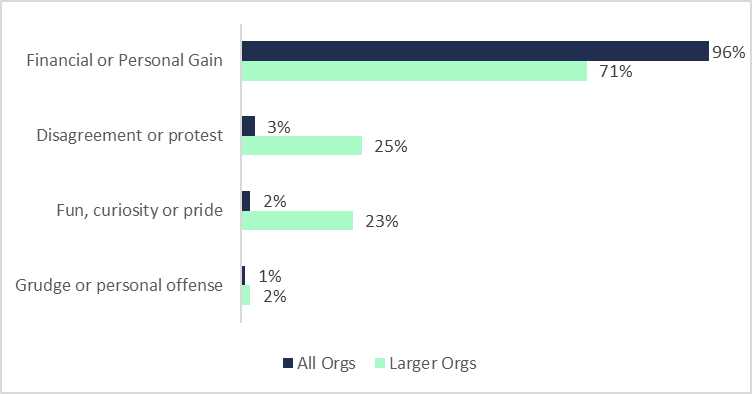
(Based on data from the 2012 Verizon Data Breach Investigations Report [DBIR])
As you can see above, Financial gain is the overwhelming primary reason for cyber attacks. This is seen in all data between 2012 and 2022. Espionage is a distant second place. The remaining attacks make up small percentages, but among them grudge sticks out as one we should discuss in more detail.
I want to discuss each of these in more detail as they apply specifically to home users. This would apply regardless of what company you work for, or if you’re self-employed. So let’s analyze each of these to understand why you are not as safe as you believe.
Financial gain
Most people think that financial gain means a hacker is going after a bank to steal money. But here’s the problem with that belief… if a hacker breaks into a bank, what’s to stop them from taking your money? Think about it, in the typical bank robber movie, did the bad guys stop when they realize that average people would be impacted? No, they steal everything in the vault. So why would a bad guy hacker only steal money from the bank and not your personal money as well?
In reality, it’s actually more complicated than this…
First, hacking into a teller machine doesn’t mean an attacker can transfer money. Most often they are getting access to a system that doesn’t even connect to where the money is stored. Second, those types of systems have a ton of security around them making it extremely difficult to hack. If they could get access to those systems, bank transfers are slow so the likelihood of success is low. Finally, there are much easier and faster ways to make money.
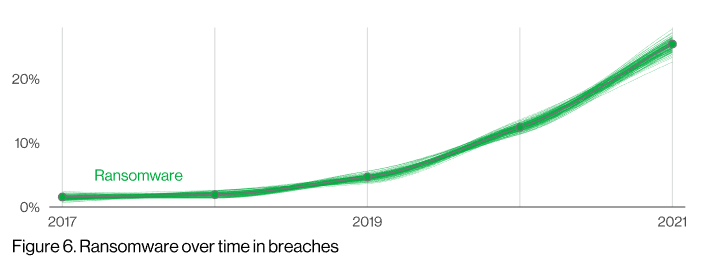
(From 2022 Verizon Data Breach Investigations Report [DBIR])
Ransomware is a type of virus which locks you out of your files by encrypting them. Typically these viruses will ask for some form of payment to “unlock” the files. Desperate users who did not have good backup practices will quite often pay the ransom. But the dirty secret is that those users only get their data back about 30% of the time when they do pay. Most experts recommend not paying and relying on good backup strategy instead.
Ransomware attacks are on the rise in a big way globally as seen in the above graph. These types of attacks are cheap and easy to execute. If you know where to go, you could go buy a Ransomware kit in a few minutes. Then just send it out to a list of emails which you can buy from a myriad of sites online.
Espionage
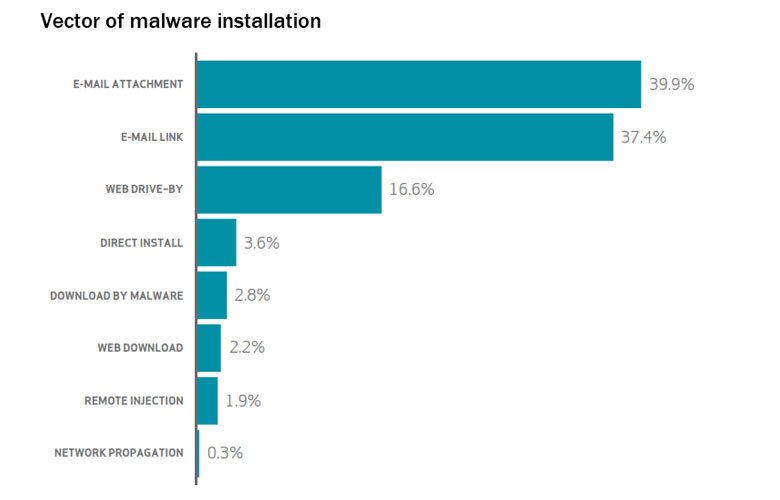
(From 2015 Verizon Data Breach Investigations Report [DBIR])
Espionage is admittedly probably not going to occur to you directly, but may target your company. Interestingly, according to the DBIR the most common vector for espionage attacks come from email. So it is important to be aware to be on the lookout for suspicious looking email.
I’m not going to go over espionage in as much detail as these attacks don’t typically target home users. If you are an employee of a larger company however, you are at risk for this type of attack. I will cover this topic in more detail in a future post.
Grudge
Grudge attacks typically starts with a bad breakup or a friendship which falls apart for some reason. One party then decides to hack into the other parties Facebook, or Twitter, or some other online presence they are aware of. They might post obscene pictures or comments on your social media, or steal private pictures. They may even use these pictures and access to your accounts as an attempt to blackmail you.
This is probably the one type of attack which is targeted more often to home users than businesses and organizations. Most people will probably never actually experience this type of attack. But it is an important type of attack to be aware of when events happen in life which might lead to anger in another person.
Many people aren’t aware but often times, when people get angry or upset, they look for help. I’ve seen job ads online where people pay experts to help them break into accounts. Whether these jobs are actually executed, I cannot say but be aware that it does happen. Just because you don’t think the person has the skill to steal your account doesn’t mean they won’t go looking for help.
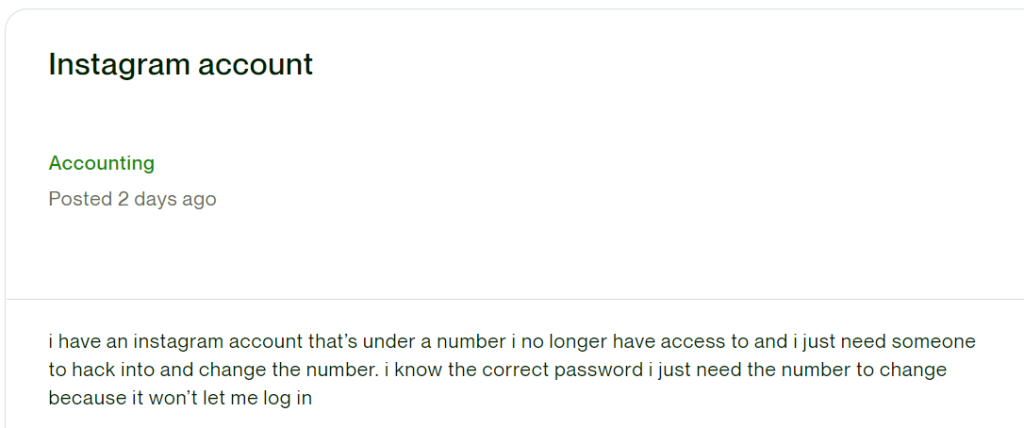
(Example posting by user requesting help accessing an account — this may be legit but anyone could post similar messages for someone else’s account)
I want to add one more point about grudge attacks. I have been speaking primarily about direct attacks against others as if from a friend. But grudge attacks do also happen against companies and employees of those companies.
This is where things get dicey, it depends on the specific motivations of the individual and their skill. Without getting too into the weeds, they may target anyone from the CEO down to the lowest level employee. Whoever might help them achieve their desired outcome could be a potential target. This makes every employee a potential target.
Other
The other category covers all other reasons for breaches which have occurred. This could include employee error or malfunctions. Most often these types of issues will not impact home users, however, the potential is there to impact home users.
For example, if a particular vulnerability is identified for a very popular home router it is likely to be exploited at a large scale by attackers. These attackers may go unnoticed for years before anything actually happens in your home network, but it gives them a foothold inside your home network.
Here’s the core issue: once a hacker has a foothold inside your home network, they can get into anything within your home network.
Conclusion
Financial gain is by far the biggest reason for cyber attacks. These types of attacks are cheap and easy to execute. This makes these types of attacks very easy to target any home user.
You very likely receive hundreds of emails a day that you don’t see because your email provider filters them out. But some will inventively make it through the spam filtering. Stay vigilant and don’t click on attachments or links if you don’t recognize the sender.
There are many more topics to cover in the #HomeSecurity series. If you want to stay up to date and keep yourself secure, sign up for my email list. I will send you updates anytime a new article is posted. If there is any topic you’d like covered in more detail, please post below.
References
Verizon Data Breach Report 2015: Top 10 Charts and Summary
The 2020 Cyber-Espionage Report pulls seven years of data to determine threat actors, motives and actions
What Motivates Hackers? Money, Secrets, and Fun
40 Worrisome Hacking Statistics that Concern Us All in 2022
2022 Data Breach Investigations Report